OUR MITIGATION PROCESS
Advanced multi-layer protection against all attack vectors
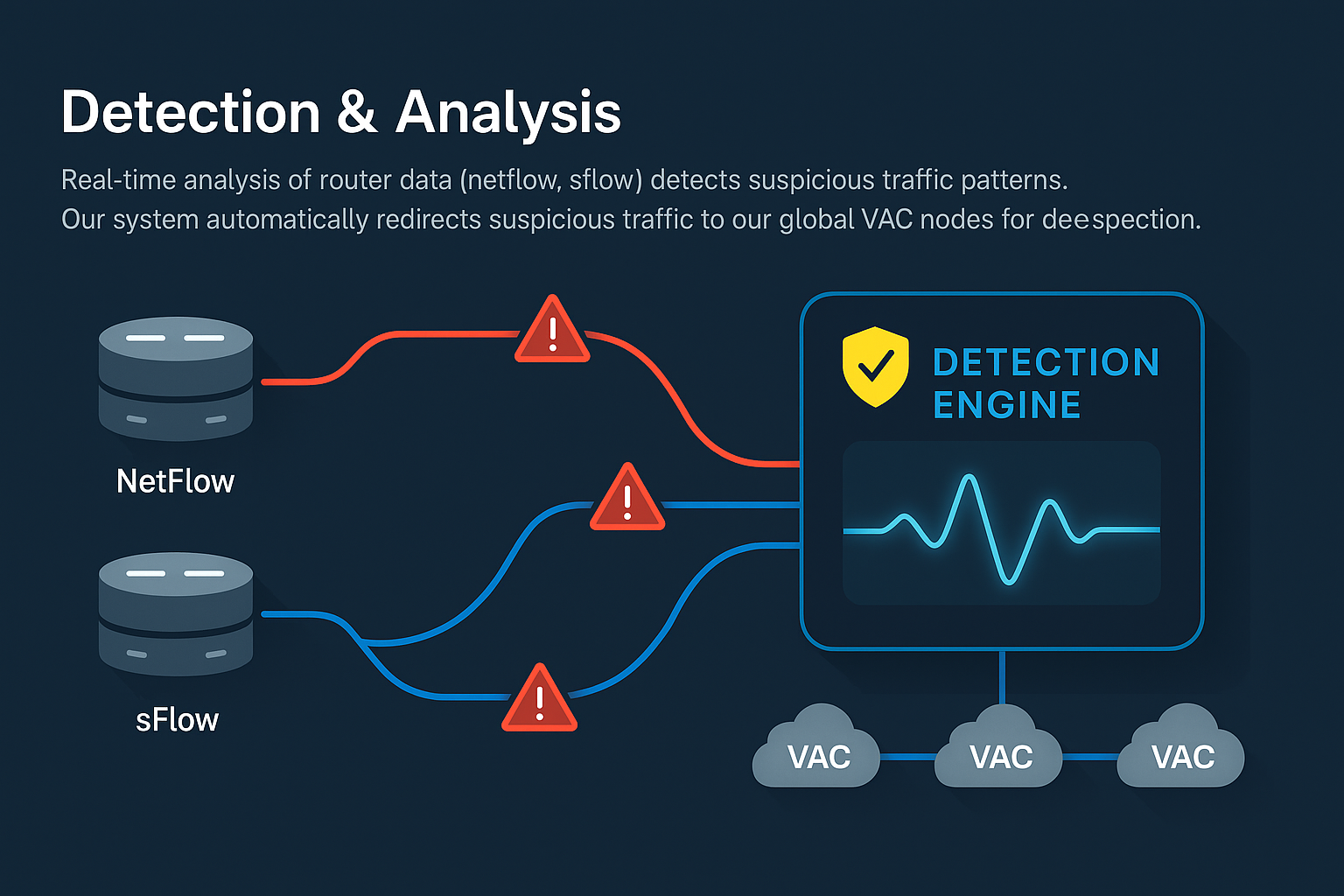
Detection & Analysis
Real-time analysis of router data (netflow, sflow) detects suspicious traffic patterns. Our system automatically redirects suspicious traffic to our global VAC nodes for deeper inspection.
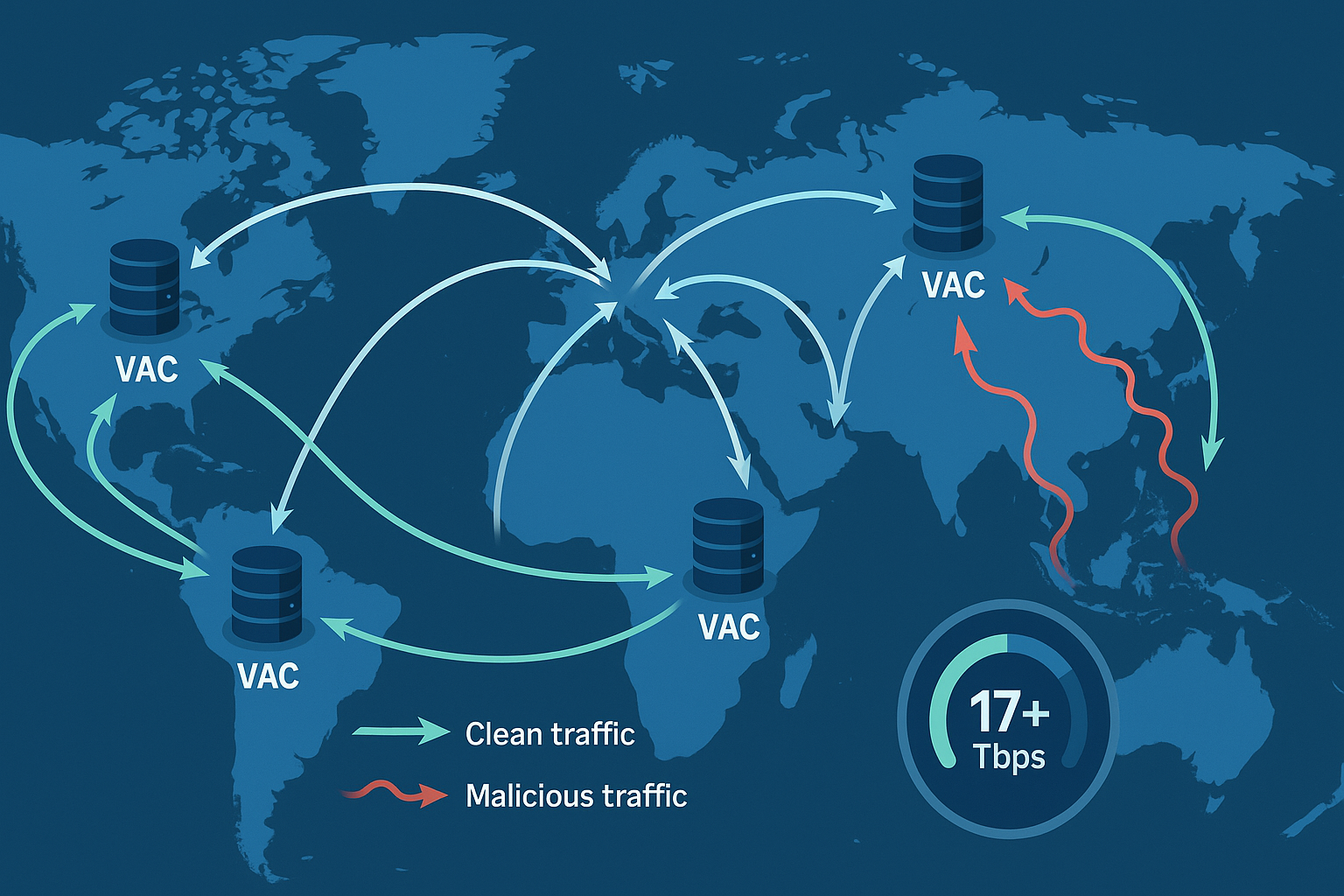
Distributed Processing
Traffic undergoes simultaneous analysis across our global network of VAC nodes, combining over 17Tbps of processing power. Our over-provisioned network ensures attack processing never impacts legitimate traffic.
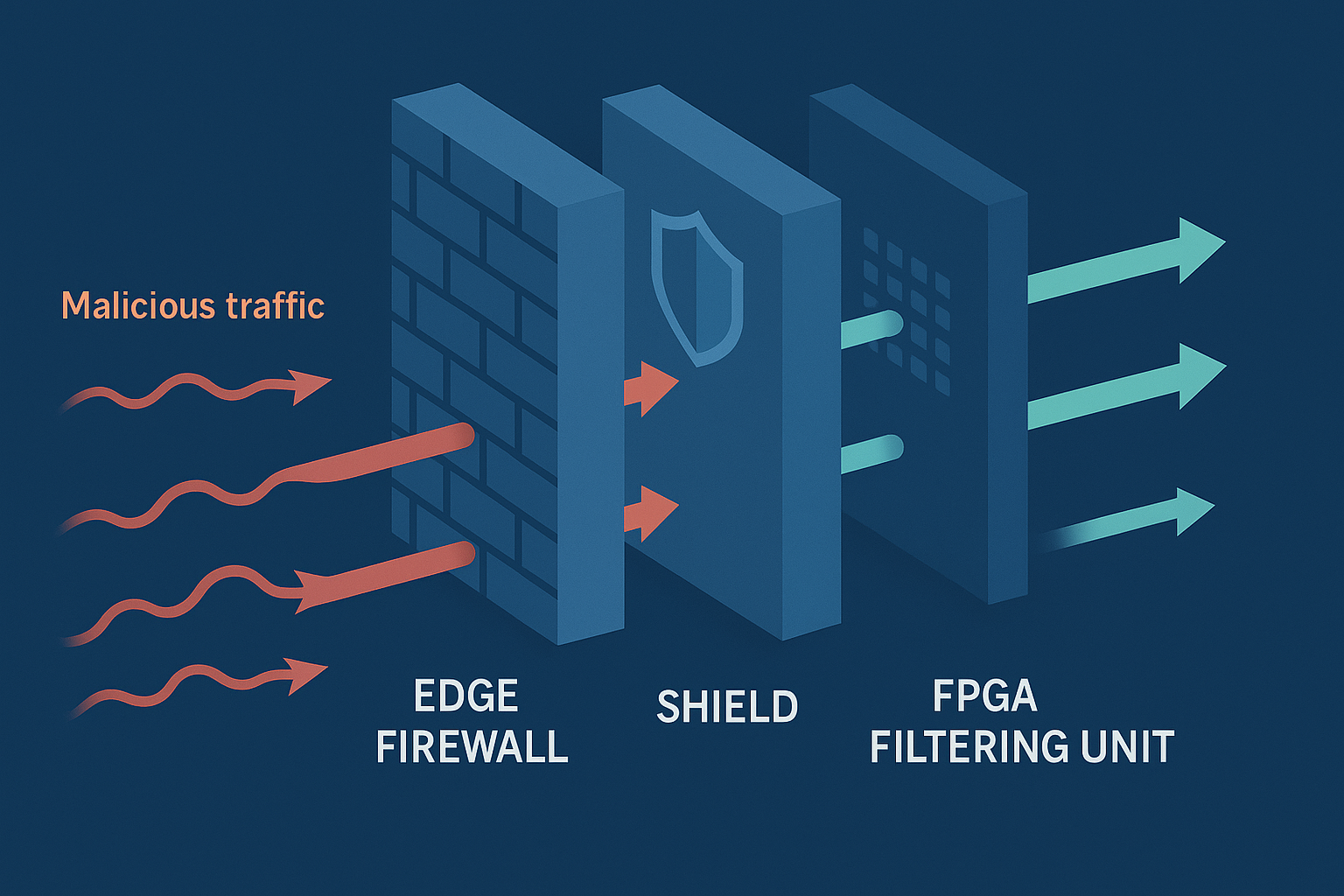
Multi-Stage Filtration
Our patented mitigation combines x86 architecture innovations with FPGA-accelerated filtering. The Edge Network Firewall, Shield, and Armor systems work in tandem to eliminate attack traffic while preserving legitimate connections.